The Facebook timeline is a feature on the social media platform that displays a user's posts and activity in chronological order. It allows users to see a history of their activity on the site, including posts, photos, videos, and other content they have shared. Some people may feel the urge to change their Facebook timeline for a variety of reasons. Some may want to clean up their timeline by removing old posts or photos that are no longer relevant, while others may want to update their timeline to reflect a change in their life, such as a new job or relationship. Additionally, some users may want to update their timeline to make it more visually appealing or to match their current interests and hobbies. It is important to note that users can edit or delete their post or photos at any time, they can also choose the level of privacy they want to set on each post. Overall, the Facebook timeline is a personal space that users can customize to their liking and preferences.
You can manifest a lot more, share easily, and control the layout more coolly, in the new facebook profile avatar. For better explaination you can visit
Facebook Timeline Details and Description (FAQ)
This new profile design that has rolled out this month is different from previous Facebook design updates. Tis time users will just love it: Timeline lets them be a designer.
The Timeline view of your profile basically divides your profile into three categories
1. Your Cover
2. Your Stories
3. Your Apps
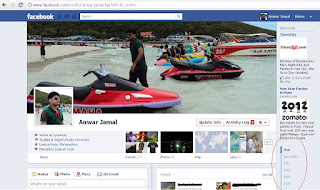
For example you can see the following Pic of a Profile page in Timeline view: (click to enlarge the picture)
You can use an stunning pic, (or any interesting one for that matter), as the cover of your profile. This will be shown in wide view. And the profile pic that was initially used will also be visible in left corner.
Your stories are your day to day happening in a time line format.
And your Apps, are the collection of your Apps that you use and its activities.
Cover Photo must tell something. Your cover is the first impression of you a user will get when he or she goes to your page. But remember, Your profile photo should be of you; your cover photo can be anything.
Edit your photos Please!. The cover is a huge space, so a high-res photo will look best. You must crop to make it better.
Click and drag on the picture so that it looks good. Tis will automatically happen when you hover your mouse over the cover picture. You will be prompted to drag and drop your picture so that u can let best portion of the Photograph to be viewed.
Be creative in choosing Cover photo.Use Web sites that help you design your own cover and share it. Sites such as MyFBCovers and SiteCanvas
It is important to note that Facebook said it will automatically push the timeline live seven days after someone signs up for the new feature. However, if folks are content with what's shared after reviewing it, they can push it live themselves at any point within that period. This was already accessible to Facebook App developers via OpenGraph API, but now Facebook itself has launched timeline feature in Full Public Release making it available to million of users together.
I am attaching a snapshot of my own profile in timeline view: (click to enlarge the image)
Or simply click here...
Get Facebook Timeline View Easily in a Click
And click on "Get It Now"
Now first of all, lets see what is Facebook TimeLine. Facebook describes it as following:
Add a cover
Edit your basic info
Jump to the past
View your activity log
See highlights from each month
Star stories you want to highlight
Add life events
Update your status
View and add photos
Share your app activity
This can be seen from the following page Help From Facebook Website Timeline
For example I have attached my Facebook Profile page. See the time line view in red circle.
Users can click on those places to go directly to specified time in your story. The new timeline feature will aggregate all your old Facebook stuff at one window and you/viewers will be able to switch between times (ie. month and year easily).
This new feature from Facebook, the largest Social Networking Website, is just awesome. And the entire outlook is just fabulous.
And just keep in mind, since this is new design, u will need time to get used to it. But during this time do not be forced to post something that u do not want everyone to see. For that purpose one simple question will pop up in ur brains that "How do I hide a story on my timeline?"
The answer is straighforward, To hide a story so that it no longer appears on your timeline:
Hover over the story and click button that appears on right of your post. (this is similar as before. only nomenclature has changed. !). Then Click Hide from Timeline.
Cheers to Facebook!
Cheers to the world!!
Please click on Advertisements because that fetches me liquid tonic used at real midnight cheers!! lol ;)
You can manifest a lot more, share easily, and control the layout more coolly, in the new facebook profile avatar. For better explaination you can visit
Facebook Timeline Details and Description (FAQ)
This new profile design that has rolled out this month is different from previous Facebook design updates. Tis time users will just love it: Timeline lets them be a designer.
The Timeline view of your profile basically divides your profile into three categories
1. Your Cover
2. Your Stories
3. Your Apps
For example you can see the following Pic of a Profile page in Timeline view: (click to enlarge the picture)
You can use an stunning pic, (or any interesting one for that matter), as the cover of your profile. This will be shown in wide view. And the profile pic that was initially used will also be visible in left corner.
Your stories are your day to day happening in a time line format.
And your Apps, are the collection of your Apps that you use and its activities.
Cover Photo must tell something. Your cover is the first impression of you a user will get when he or she goes to your page. But remember, Your profile photo should be of you; your cover photo can be anything.
Edit your photos Please!. The cover is a huge space, so a high-res photo will look best. You must crop to make it better.
Click and drag on the picture so that it looks good. Tis will automatically happen when you hover your mouse over the cover picture. You will be prompted to drag and drop your picture so that u can let best portion of the Photograph to be viewed.
Be creative in choosing Cover photo.Use Web sites that help you design your own cover and share it. Sites such as MyFBCovers and SiteCanvas
It is important to note that Facebook said it will automatically push the timeline live seven days after someone signs up for the new feature. However, if folks are content with what's shared after reviewing it, they can push it live themselves at any point within that period. This was already accessible to Facebook App developers via OpenGraph API, but now Facebook itself has launched timeline feature in Full Public Release making it available to million of users together.
I am attaching a snapshot of my own profile in timeline view: (click to enlarge the image)
Activating Timeline View
How to switch / convert to Cover page View / time line view in Facebook
You can activate this type of profile by visiting the page described above.Or simply click here...
Get Facebook Timeline View Easily in a Click
And click on "Get It Now"
Now first of all, lets see what is Facebook TimeLine. Facebook describes it as following:
What is a new Timeline view in facebook?
Your timeline is your collection of the photos, stories, and experiences that tell your story. Here are some of the things you can do on your timeline:Add a cover
Edit your basic info
Jump to the past
View your activity log
See highlights from each month
Star stories you want to highlight
Add life events
Update your status
View and add photos
Share your app activity
This can be seen from the following page Help From Facebook Website Timeline
For example I have attached my Facebook Profile page. See the time line view in red circle.
Users can click on those places to go directly to specified time in your story. The new timeline feature will aggregate all your old Facebook stuff at one window and you/viewers will be able to switch between times (ie. month and year easily).
This new feature from Facebook, the largest Social Networking Website, is just awesome. And the entire outlook is just fabulous.
And just keep in mind, since this is new design, u will need time to get used to it. But during this time do not be forced to post something that u do not want everyone to see. For that purpose one simple question will pop up in ur brains that "How do I hide a story on my timeline?"
The answer is straighforward, To hide a story so that it no longer appears on your timeline:
Hover over the story and click button that appears on right of your post. (this is similar as before. only nomenclature has changed. !). Then Click Hide from Timeline.
Cheers to Facebook!
Cheers to the world!!
Please click on Advertisements because that fetches me liquid tonic used at real midnight cheers!! lol ;)